Touch ID. Login with Facebook. ATM machines. Corporate directory services. What’s the commonality? Digital identity! We live in an increasingly connected world where we continuously consume information. From accessing email, checking the bank statement, to streaming music online, we’re constantly hitting APIs that securely retrieve our data from on-premises and the cloud. Digital identity is the online representation of a person, organization, or a machine, and it is what gives us access to the data we use daily. It’s a part of our lives, whether at work or at home. Here’s a brief overview of identity, why it's vital to information security, and why you should know more about it.
Identity back then
Let's go back to the year 2000, when the majority of people with internet access are still using dialup. Millions are getting online for the first time, and internet companies are having their first big moments on the stock market. Some innovative companies such as Amazon and eBay are able to establish themselves in the new online marketplace. Others, like WebVan and Pets.com, are perhaps ahead of their time.
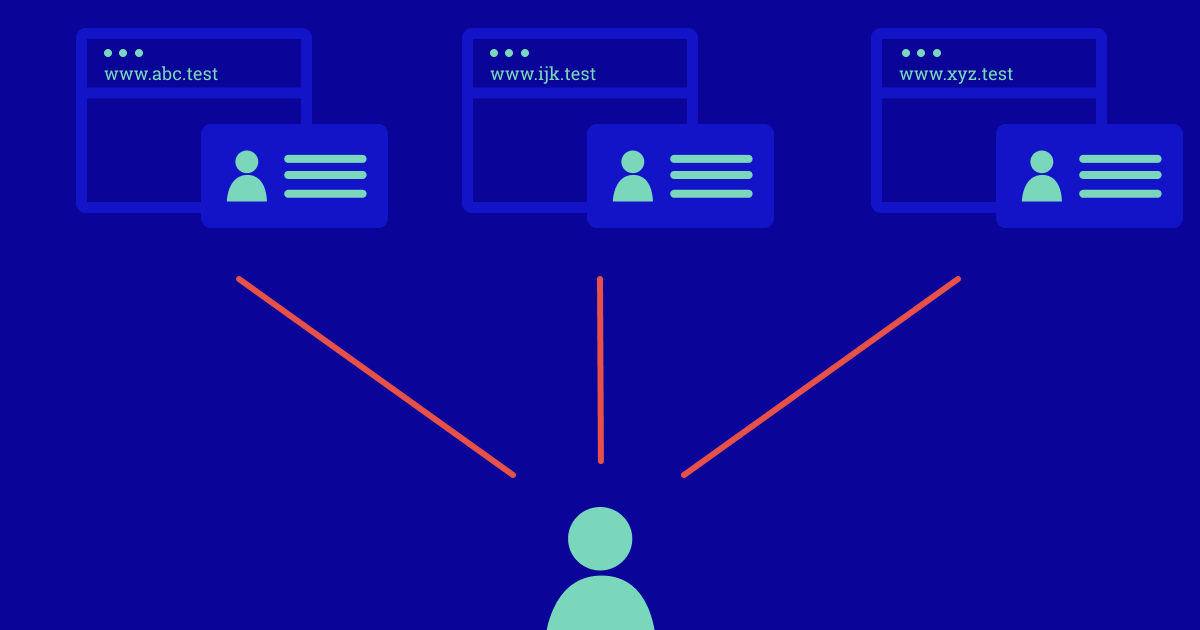
Figure 1: Each website has a separate digital identity of you
During this era, you have separate digital identities for each website. This requires you to keep track of multiple usernames and passwords, which encourages password reuse. Reusing passwords jeopardizes the security of all your websites if just one of them is compromised.
If you happen to work at a company or institution with a substantial network, you can expect to be logging in to your computer via a directory service solution such as Novell Directory Services, which gives your corporate identity access to file and print services across the local-area network (LAN). Network perimeters and passwords are your primary means to protect your local corporate data; firewalls keep the bad guys out while you access your apps and data within the confines of your trusted network. But your identity only exists in the space you are currently in—a single website or a corporate, hard-wired LAN.
In 2001, the Enron accounting scandal makes headlines due to inflated earnings reports and fraud. The scandal reveals Enron’s weak internal controls which enabled its employees to act dishonestly. Because of this and other scandals, Congress passes the Sarbanes-Oxley Act, which, if you are a publicly-traded company, includes requirements that make executives liable for their employees’ access controls. This and other regulations encourage the adoption of identity and access management systems (IAM) to govern users and assign access to needed resources.
Identity now
The 90s era requirement of only needing access to your on-premises applications and data changes quickly. With the mid-2000s, comes an increasing usage of applications that are hosted outside of your network. Software as a service (SaaS) applications like Concur (now SAP Concur), which manages corporate travel and expenses, become popular. In 2006, Amazon Web Services begins offering cloud computing services, enabling you to run applications on servers and store data on a pay-as-you-go basis, with all your information based in offsite data centers. Today, companies ranging from startups to enterprises are migrating their workloads to run entirely in the cloud.
On the consumer side, the iPhone comes on the scene in 2007, kickstarting the era of smartphones and tablets. Suddenly, you can have immediate access to information through your mobile browser or the many apps available on your device. These devices increasingly become the concern of corporate IT departments as employees connect to internal networks using devices that IT has no control over.
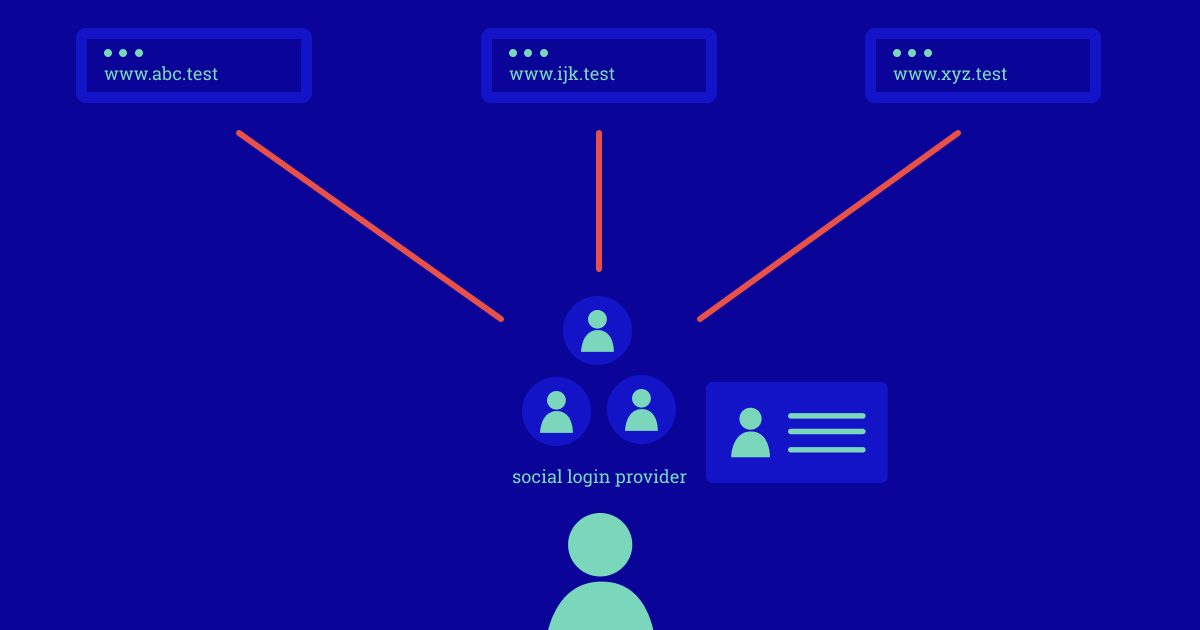
Figure 2: Social login enables you to centralize your digital identity
By 2009, social login becomes available, which allows you to login to your apps and websites through your social identity such as Twitter or Facebook. This is made possible by OAuth, which is a standard that allows you to authorize access to applications without sharing your password. Social login enables you to have your consumer identity hosted on the provider of your choice, improving security through less reliance on passwords.
The advent of SaaS, cloud computing, and mobile means that your company now has to manage employees’ access for when the data resides outside the corporate network—and potentially the access of your company’s customers as well. And data cannot be assumed secure when inside the perimeter; the rising prevalence of phishing, social engineering, malware, and insider threats blur further the perimeter of trust.
With the network perimeter no longer solely defining what is safe, and with increasing acceptance and adoption of strong authentication, corporations are now beginning to consider a Zero Trust model. Zero Trust states that the security of your data cannot merely rely on the safety of your network. Instead, data security is highly dependent on strong authentication controls and fine-grained authorization—in other words, we’re confident that they are who we think they are and have only the permissions they need for access.
Passwords as a single factor of authentication are often not enough. It is increasingly easy for attackers to crack a weak password in seconds or obtain it through clever methods such as phishing scams. The importance of multi-factor authentication (MFA) has therefore increased even outside of highly-secured institutions such as banks and government agencies. MFA makes it much more difficult for someone to bypass your authentication controls.
For example, if your password is your first factor and a virtual or physical security token is your second factor, an attacker will need both in order to compromise your identity. The recent widespread introduction of passwordless authentication through the use of biometric factors such as fingerprints makes it possible to avoid passwords altogether.
Now strong authentication is even easier on supported devices such as smartphones, tablets, and laptops. MFA and passwordless authentication work in harmony with the Zero Trust model to further secure your confidential data regardless of where it is located. Combined with the rise of comprehensive identity and access management systems, you now have increasingly secure solutions for managing identities, their access rights, and the data you needed to protect.
How does identity affect you
These trends haven’t slowed down—the amount of applications and data available to us is exploding, making it harder to keep track of access to that data without dedicated identity and access management systems. And as entire companies such as Twitter, Facebook, and Slack are declaring remote workforces as the new normal due to the global pandemic, Zero Trust and identity are even more important.
If you’re developing a multi-user consumer application, you’ll want to consider if offering them the ability to login with their social identity makes sense from a security and usability standpoint. The benefits are that it reduces friction during the signup process, which ensures you convert more curious customers to full time users. It also offloads some of the work of identity management and security to large, well resourced companies. You’ll also need to assess which customer identity and access management solutions (CIAM) are right for you to help you manage access for the potentially thousands or millions of users that will use your app. Amazon Cognito and Auth0 are some of the solutions in the CIAM space that help with this.
If you have a job in identity management, such as managing your corporate directory, sooner or later you’ll have to grapple with how you’ll implement MFA. And you’ll need to consider how your employees will access the cloud, even if your identity store remains on-premises. And you’ll have to dive into identity federation, which means understanding how your directory service will integrate with your cloud provider and what minimum permissions are required to enable employees to do their job.
Where do I go from here
Since identity is a large and complex topic, a great place for you to start is with educational resources! You’ll want to familiarize yourself with the basics. It's important to understand authentication and authorization as these terms are used all the time when learning about identity and IAM solutions. IDPro, which is a not-for-profit association of identity professionals, has educational resources that you can access online that address this. If you’re a developer, there’s also masterclass videos on OAuth which you’ll want to watch if enabling social login to your app through a supported OAuth provider such as Google, Facebook, or Github. If you’re an IAM admin or engineer, you’ll want to read up on MFA, single-sign on (SSO), and federation.
I’ve also helped develop a course, “Introduction to AWS Identity and Access Management,” which introduces you to these basic identity topics and what they look like in AWS cloud. They’re free on Coursera and edX. AWS Training and Certification also offers free relevant and comprehensive security training to help you innovate with confidence and advance your career. For more information, please visit here.
Additional Resources
- Okta - Identity 101 Index - an index of identity terminology
- IDPro educational resources - additional resources for identity practitioners
- IDPro Body of Knowledge - identity practitioner concepts and terms
- Zero Trust Networks - book by by Evan Gilman, Doug Barth
- Zero Trust architectures: An AWS perspective- how Zero Trust looks in AWS
- Learn about AWS Security- free and fee-based AWS security training
- AWS Certified Security, Specialty exam - validates knowledge of securing the AWS platform
- AWS Identity services - Identity-related services on AWS